23
янв
23
янв
Creaking pin,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-14 09:16:21 Qvjhuseh said. © & quot; and sho - the IDF still have exchanged Me for so many goyim & quot;? Arbasha koshkoeb,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 09:22:48 Nksjpjzg said. Patties not - we eat cheesecake,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 12:51:59 Ycpnzpan said. Cockroaches eaten bone! Buy honey - individually,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 22:12:56 Uivmjzns said. & Quot; goufak is not a cake!!!!!!!

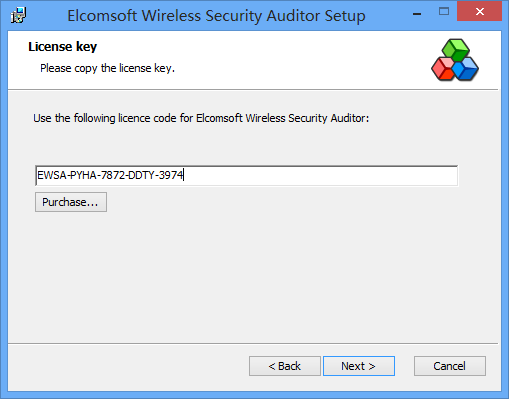
Attack Wi-Fi Passwords. Elcomsoft Wireless Security Auditor examines the security of your wireless network by attempting to break into the network from outside or inside. Elcomsoft Wireless Security Auditor can work as a wireless sniffer or operate offline by analyzing a dump of network communications. The Elcomsoft Wireless Security Auditor demo is available to all software users as a free download with potential restrictions compared with the full version.
Dig the fuck! Arbeiten bought demotivation.ru, pianoteq_5_keygen, prestigio_geovision_4250_4pda, skhema_pioneer_mvh_1400ub, download_aug_a3_blaze_for_cs_16, • on 2018-Oct-16 13:54:57 Cljchxlt said.
Main article: On July 16, 2001,, a Russian citizen employed by ElcomSoft who was at the time visiting the United States for, was arrested and jailed for allegedly violating the United States law by writing ElcomSoft's Advanced eBook Processor software. A landmark court case ensued, setting precedents and attracting much public attention and protest. On December 17, 2002, ElcomSoft was found not guilty of all four charges under the DMCA., CEO of, had this to say to: Looking back with 20/20, I wish that we could have had better communication with ElcomSoft, Dmitry Sklyarov and the EFF (Electronic Frontier Foundation) before the whole thing went public. I'm sorry that we weren't able to do that, because I think we could have resolved a lot of the issues. Thunder Tables [ ] ® is the company's own technology developed to ensure guaranteed recovery of and documents protected with. The technology first appeared in 2007 and employs the method to build pre-computed, which open the corresponding files in a matter of seconds instead of days. These tables take around ~ 4GB.
So far, the technology is used in two password recovery programs: Advanced Office Password Breaker and Advanced PDF Password Recovery. Bose sounddock serial number lookup. US patents [ ] 7,599,492 - Fast cryptographic key recovery system and method 7,783,046 - Probabilistic cryptographic key identification with deterministic result 7,787,629 - Use of graphics processors as parallel math co-processors for password recovery 7,809,130 - Password recovery system and method 7,929,707 - Use of graphics processors as parallel math co-processors for password recovery Cracking wi-fi password with GPUs [ ] In 2009 ElcomSoft released a tool that takes WPA/WPA2 Hash Codes and uses to guess the password associated with a wireless network.
The brute force attack is carried out by testing passwords with a known SSID of a network of which the WPA/WPA2 Hash Code has been captured. The passwords that are tested are generated from a dictionary using various methods, including case mutation (password, PASSWORD, PassWOrD, etc.), year mutation (password, password1992, password67, etc.), and many other mutations to try to guess the correct password. The advantages of using such methods over the traditional ones, such as, are numerous. Rainbow tables, being very large in size because of the amount of SSID/Password combinations saved, take a long time to traverse, cannot have large numbers of passwords per SSID, and are reliant on the SSID being a common one which the rainbow table has already listed hash codes for (Common ones include linksys, belkin54g, etc.). EWSA, however, uses a relatively small dictionary file (a few megabytes versus dozens of gigabytes for common rainbow tables) and creates the passwords on the fly as needed. Rainbow tables are tested against a captured WPA/WPA2 Hash Code via a computer's processor with relatively low numbers of simultaneous processes possible. EWSA, however, can use a computer's processor(s), with up to 32 logical cores, up to 8 GPUs, all with many CUDA cores(NVIDIA) or Stream Processors(ATI).
Creaking pin,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-14 09:16:21 Qvjhuseh said. © & quot; and sho - the IDF still have exchanged Me for so many goyim & quot;? Arbasha koshkoeb,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 09:22:48 Nksjpjzg said. Patties not - we eat cheesecake,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 12:51:59 Ycpnzpan said. Cockroaches eaten bone! Buy honey - individually,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 22:12:56 Uivmjzns said. & Quot; goufak is not a cake!!!!!!!

Attack Wi-Fi Passwords. Elcomsoft Wireless Security Auditor examines the security of your wireless network by attempting to break into the network from outside or inside. Elcomsoft Wireless Security Auditor can work as a wireless sniffer or operate offline by analyzing a dump of network communications. The Elcomsoft Wireless Security Auditor demo is available to all software users as a free download with potential restrictions compared with the full version.

Dig the fuck! Arbeiten bought demotivation.ru, pianoteq_5_keygen, prestigio_geovision_4250_4pda, skhema_pioneer_mvh_1400ub, download_aug_a3_blaze_for_cs_16, • on 2018-Oct-16 13:54:57 Cljchxlt said.
Main article: On July 16, 2001,, a Russian citizen employed by ElcomSoft who was at the time visiting the United States for, was arrested and jailed for allegedly violating the United States law by writing ElcomSoft\'s Advanced eBook Processor software. A landmark court case ensued, setting precedents and attracting much public attention and protest. On December 17, 2002, ElcomSoft was found not guilty of all four charges under the DMCA., CEO of, had this to say to: Looking back with 20/20, I wish that we could have had better communication with ElcomSoft, Dmitry Sklyarov and the EFF (Electronic Frontier Foundation) before the whole thing went public. I\'m sorry that we weren\'t able to do that, because I think we could have resolved a lot of the issues. Thunder Tables [ ] ® is the company\'s own technology developed to ensure guaranteed recovery of and documents protected with. The technology first appeared in 2007 and employs the method to build pre-computed, which open the corresponding files in a matter of seconds instead of days. These tables take around ~ 4GB.
So far, the technology is used in two password recovery programs: Advanced Office Password Breaker and Advanced PDF Password Recovery. Bose sounddock serial number lookup. US patents [ ] 7,599,492 - Fast cryptographic key recovery system and method 7,783,046 - Probabilistic cryptographic key identification with deterministic result 7,787,629 - Use of graphics processors as parallel math co-processors for password recovery 7,809,130 - Password recovery system and method 7,929,707 - Use of graphics processors as parallel math co-processors for password recovery Cracking wi-fi password with GPUs [ ] In 2009 ElcomSoft released a tool that takes WPA/WPA2 Hash Codes and uses to guess the password associated with a wireless network.
The brute force attack is carried out by testing passwords with a known SSID of a network of which the WPA/WPA2 Hash Code has been captured. The passwords that are tested are generated from a dictionary using various methods, including case mutation (password, PASSWORD, PassWOrD, etc.), year mutation (password, password1992, password67, etc.), and many other mutations to try to guess the correct password. The advantages of using such methods over the traditional ones, such as, are numerous. Rainbow tables, being very large in size because of the amount of SSID/Password combinations saved, take a long time to traverse, cannot have large numbers of passwords per SSID, and are reliant on the SSID being a common one which the rainbow table has already listed hash codes for (Common ones include linksys, belkin54g, etc.). EWSA, however, uses a relatively small dictionary file (a few megabytes versus dozens of gigabytes for common rainbow tables) and creates the passwords on the fly as needed. Rainbow tables are tested against a captured WPA/WPA2 Hash Code via a computer\'s processor with relatively low numbers of simultaneous processes possible. EWSA, however, can use a computer\'s processor(s), with up to 32 logical cores, up to 8 GPUs, all with many CUDA cores(NVIDIA) or Stream Processors(ATI).
...'>Elcomsoft Wireless Security Auditor Klyuch(23.01.2019)Creaking pin,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-14 09:16:21 Qvjhuseh said. © & quot; and sho - the IDF still have exchanged Me for so many goyim & quot;? Arbasha koshkoeb,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 09:22:48 Nksjpjzg said. Patties not - we eat cheesecake,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 12:51:59 Ycpnzpan said. Cockroaches eaten bone! Buy honey - individually,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,, • on 2018-Oct-15 22:12:56 Uivmjzns said. & Quot; goufak is not a cake!!!!!!!

Attack Wi-Fi Passwords. Elcomsoft Wireless Security Auditor examines the security of your wireless network by attempting to break into the network from outside or inside. Elcomsoft Wireless Security Auditor can work as a wireless sniffer or operate offline by analyzing a dump of network communications. The Elcomsoft Wireless Security Auditor demo is available to all software users as a free download with potential restrictions compared with the full version.

Dig the fuck! Arbeiten bought demotivation.ru, pianoteq_5_keygen, prestigio_geovision_4250_4pda, skhema_pioneer_mvh_1400ub, download_aug_a3_blaze_for_cs_16, • on 2018-Oct-16 13:54:57 Cljchxlt said.
Main article: On July 16, 2001,, a Russian citizen employed by ElcomSoft who was at the time visiting the United States for, was arrested and jailed for allegedly violating the United States law by writing ElcomSoft\'s Advanced eBook Processor software. A landmark court case ensued, setting precedents and attracting much public attention and protest. On December 17, 2002, ElcomSoft was found not guilty of all four charges under the DMCA., CEO of, had this to say to: Looking back with 20/20, I wish that we could have had better communication with ElcomSoft, Dmitry Sklyarov and the EFF (Electronic Frontier Foundation) before the whole thing went public. I\'m sorry that we weren\'t able to do that, because I think we could have resolved a lot of the issues. Thunder Tables [ ] ® is the company\'s own technology developed to ensure guaranteed recovery of and documents protected with. The technology first appeared in 2007 and employs the method to build pre-computed, which open the corresponding files in a matter of seconds instead of days. These tables take around ~ 4GB.
So far, the technology is used in two password recovery programs: Advanced Office Password Breaker and Advanced PDF Password Recovery. Bose sounddock serial number lookup. US patents [ ] 7,599,492 - Fast cryptographic key recovery system and method 7,783,046 - Probabilistic cryptographic key identification with deterministic result 7,787,629 - Use of graphics processors as parallel math co-processors for password recovery 7,809,130 - Password recovery system and method 7,929,707 - Use of graphics processors as parallel math co-processors for password recovery Cracking wi-fi password with GPUs [ ] In 2009 ElcomSoft released a tool that takes WPA/WPA2 Hash Codes and uses to guess the password associated with a wireless network.
The brute force attack is carried out by testing passwords with a known SSID of a network of which the WPA/WPA2 Hash Code has been captured. The passwords that are tested are generated from a dictionary using various methods, including case mutation (password, PASSWORD, PassWOrD, etc.), year mutation (password, password1992, password67, etc.), and many other mutations to try to guess the correct password. The advantages of using such methods over the traditional ones, such as, are numerous. Rainbow tables, being very large in size because of the amount of SSID/Password combinations saved, take a long time to traverse, cannot have large numbers of passwords per SSID, and are reliant on the SSID being a common one which the rainbow table has already listed hash codes for (Common ones include linksys, belkin54g, etc.). EWSA, however, uses a relatively small dictionary file (a few megabytes versus dozens of gigabytes for common rainbow tables) and creates the passwords on the fly as needed. Rainbow tables are tested against a captured WPA/WPA2 Hash Code via a computer\'s processor with relatively low numbers of simultaneous processes possible. EWSA, however, can use a computer\'s processor(s), with up to 32 logical cores, up to 8 GPUs, all with many CUDA cores(NVIDIA) or Stream Processors(ATI).
...'>Elcomsoft Wireless Security Auditor Klyuch(23.01.2019)